Certificate of Analysis CoA
This topic is part of the SG Systems Global regulatory & operations glossary.
Updated October 2025 • Cross-Industry (Pharma, Food, Supplements, Devices, Cosmetics, Chemicals) • LIMS / QMS / MES • Data Integrity, e-Signatures, Supplier COA Verification
A Certificate of Analysis (CoA) is the authoritative, lot-specific statement of conformance that presents tested results against approved specifications for a product, intermediate, raw material, or component. It unifies laboratory data, method/version context, acceptance criteria, sampling plans, and signatures into a legally relevant record that enables Batch Release, import/export clearance, and downstream use. A defensible CoA does more than list numbers: it integrates lot genealogy, deviations/OOS handling, Change Control history affecting the lot, and the current effective Bill of Materials (BOM), recipe, and label claims. In modern operations, the CoA is compiled automatically from controlled sources (eBMR/eBR, LIMS, QMS) and issued in human-readable (PDF) and machine-readable (JSON/CSV) formats with controls to prevent tampering under 21 CFR Part 11 / EU Annex 11.
“If the CoA isn’t generated from source-truth and bound to the lot genealogy, it’s not assurance—it’s stationery.”
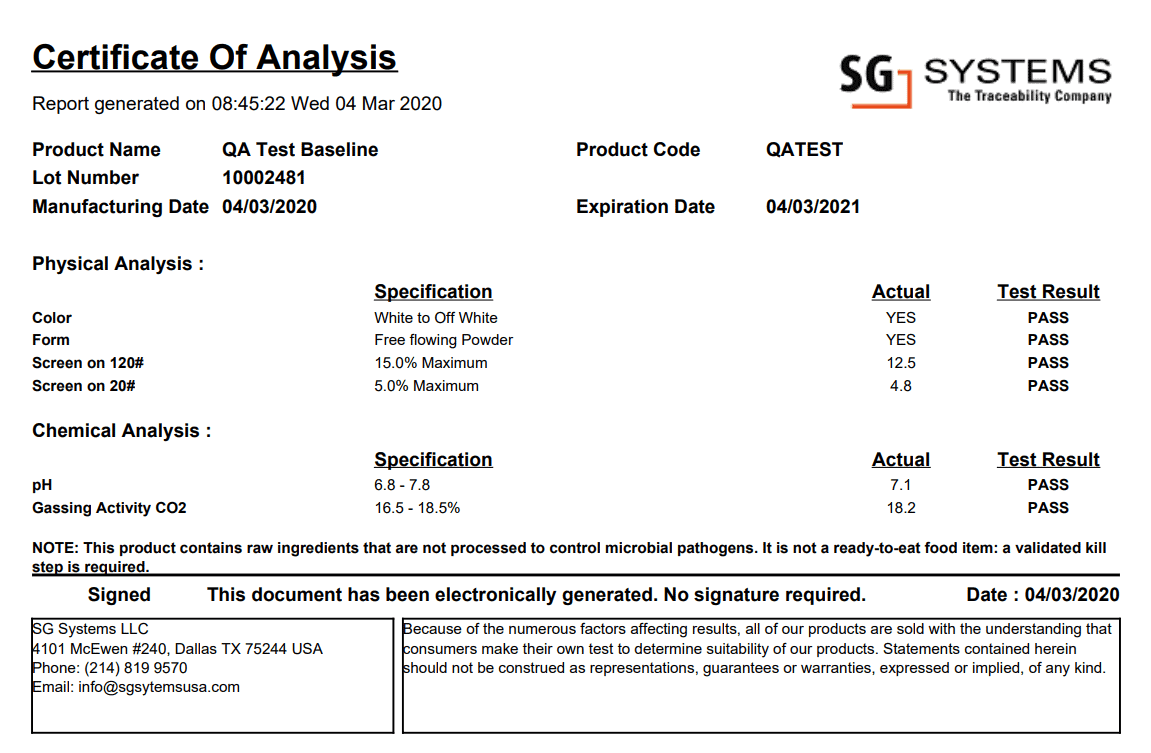
1) What a Certificate of Analysis (CoA) Actually Is
A CoA certifies that a specific lot (or serialised unit for devices) meets identity, purity, quality, safety, and performance specifications defined in approved master data. It usually summarises the applicable regulatory framework (for example, 21 CFR Part 211, 21 CFR Part 111, 21 CFR Part 117, ISO 13485, ISO/IEC 17025) and makes the release decision transparent to customers, regulators, and auditors.
Typical CoAs cover: product name and strength, dosage form or product type; lot/serial number; manufacturing and expiry/retest dates; storage conditions; specification and method references; sampling plan; test list; numerical results with units and rounding rules; pass/fail determinations; and reviewer/approver details. For pharmaceuticals and APIs, the CoA typically includes identification, assay/potency, related substances, residual solvents, water content, microbiological attributes, and physical tests (appearance, pH, viscosity). For food and supplements, allergen declarations, label-claim verification, and micro are central. For medical devices, the CoA often highlights sterilisation parameters, bioburden/endotoxin limits, functional tests, and packaging/UDI checks tied back to the Device History Record (DHR).
CoA vs. CoC vs. SDS vs. specification sheets. A Certificate of Conformance (CoC) generally attests that a product meets a defined standard but does not always present analytical results. A CoA must present actual test data. Safety Data Sheets (SDS) communicate hazards and handling requirements but are not proof of lot-level conformance. Marketing datasheets or “typical properties” are likewise not CoAs. Confusing these documents is a common gap in supplier and customer audits.
| Section | What it covers | Linked controls |
|---|---|---|
| Header | Product, lot/serial, strength, dosage form, site, dates, storage | Products & Formulas • Lot Traceability |
| Specification summary | Identity, assay, impurities, micro, physical tests with limits | QbD • QMS |
| Test results | Method IDs, units, numeric results, pass/fail, comments | Lab Tests & Review • TMV |
| Sampling & status | Sampling plan, chain of custody, status (Quarantine/Released) | GMP Sampling Plans • Quarantine / Hold |
| Signatures & declarations | Reviewer/approver, e-signatures, claims (GMO-free, allergen, etc.) | Audit Trail • Record Retention |
In the sample CoA above, these sections typically appear in a predictable order: a clearly labelled header, a table of attributes and specifications, a table of results, and a sign-off block. Consistent layout reduces interpretation errors at receiving sites and supports automated parsing by customer systems.
Minimum credible contents. As a baseline, a defensible CoA should clearly show: product/strength/SKU; lot/serial; manufacturing and expiry/retest dates; site of manufacture; specification version; test list with method IDs and units; sampling plan or reference; numerical results; pass/fail; reviewer/approver names and e-signatures; storage/transport conditions; and critical declarations (allergen, GMO, BSE/TSE, residual solvents, restricted impurities). Optional but recommended: stability status, cross-contamination controls, and supply-chain identifiers supporting end-to-end traceability.
2) Lifecycle & Governance: From Specification to Archival
A credible CoA lifecycle spans definition → generation → review/approval → issuance → retention → complaint/recall linkage. Each stage should be clearly owned within the Quality Management System (QMS) and supported by procedures, training, and systems.
Definition. Quality, technical, and regulatory teams define specifications, mapping attributes and limits to filings, pharmacopeias, and label claims. Sampling plans align with AQL or other statistical criteria and with sector-specific requirements (for example, identity testing expectations in 21 CFR Part 111). Methods carry validation status and version control; changes are governed through Change Control and linked to Process Validation, CPV, and APR/PQR.
Generation. In a mature stack, LIMS posts approved results with instrument, calibration, and analyst trace; MES/eBMR contributes batch context (yield, alarms, start/stop times, Cleaning Validation status, Environmental Monitoring summaries where relevant). Any OOS or OOT results must be addressed through QMS workflows (Deviations/NCs, CAPA) before the CoA is finalised.
Review & approval. Qualified reviewers and approvers perform structured checks: data completeness, method/spec alignment, trending vs historical data (often via SPC charts and X-bar/R charts), open deviations, and final disposition. Approval follows documented Approval Workflows with e-signatures compliant with Part 11/Annex 11 and the applicable device, food, or cosmetic rules.
Issuance & retention. Once released, the CoA should be immutable: updates require a new revision, not silent edits. Distribution can be via PDF, customer portals, EDI/ASN attachments, or QR/GS1 Digital Link references on labels. Under Record Retention & Archival policies, CoAs must remain retrievable for the full product lifecycle plus statutory retention periods, including for mock or real recalls.
Complaint & recall linkage. For returns/RMAs, complaints, or recalls, the CoA is one of the first records requested by regulators and customers. It must be linkable to the batch record, distribution records, and traceability chain, making gaps here highly visible.
3) Data Structure, Integrity & Traceability
CoA credibility lives or dies on provenance and immutability. Every result should be traceable back to a specific sample, method version, instrument, and analyst with an unbroken audit trail. Edits, overrides, or result re-calculations must be reason-coded and time-stamped, reflecting ALCOA+ principles (Attributable, Legible, Contemporaneous, Original, Accurate + Complete, Consistent, Enduring, Available).
Structured, machine-readable CoAs. Many organisations now maintain a “data first, document second” model where structured CoA payloads feed customer systems and portals. A pragmatic schema includes:
- Header fields (product, lot/serial, spec ID/version, site, dates, storage conditions, status).
- Test array (attribute ID, method ID, units, nominal/target, result, limit set, pass/fail, comments).
- Sampling section (plan ID, composite rules, strata, sample size, chain of custody IDs).
- Attachments (chromatograms, spectra, micro images, stability summaries) and stability bracket references.
- Signatures (reviewer/approver, timestamps, certificate chain) and a cryptographic hash that also appears on the PDF.
The sample CoA graphic demonstrates this structure visually: a clear header, followed by a structured test table where each row corresponds to an attribute (for example, identity, assay, impurities) and shows “Result vs. Specification.” This format is easily mapped into JSON or XML fields for automated intake by customer LIMS and ERP platforms.
Linking to genealogy, warehouse status & serialization. The CoA should reference the effective recipe/spec, labeling control, and packaging configuration in force at the time of release. Integration with Bin / Location Management, Serialization, and SSCC ensures the CoA issued to a customer matches the actual units shipped, not just the intended ones. This is central to DSCSA and global traceability regimes.
4) Sampling Plans & Method Validation
Sampling defines whether results can legitimately represent a full lot. Whether using attribute sampling for micro, variable sampling for assay, or risk-based schemes under GMP sampling plans, the basis should be referenced on or from the CoA. Where stratified sampling is used (for example, multiple container strata, top/middle/bottom drum samples, time-based grabs), the strata and composite logic should be documented so that retesting or investigations can reconstruct exactly what was done.
Method validation & verification. Methods used to generate CoA data must be shown to be fit for purpose. Under Test Method Validation (TMV) and ISO/IEC 17025, parameters such as specificity, accuracy, precision, linearity, range, and robustness are documented and controlled. When compendial methods change or local variants are adopted, verification activities, risk assessments, and Change Control records must show that the CoA output remains interpretable years later.
Retesting and result repeats. When OOS or suspect results occur, any retesting must follow a controlled procedure, often tied to Quality Risk Management (QRM) and Root Cause Analysis (RCA). The final CoA should present the valid result while retaining a clear reference back to the investigation, not rewriting history.
5) Regulatory Expectations & Sector-Specific Patterns
Pharma/API. Under 21 CFR 210/211, ICH Q7, and ICH Q10, CoAs must support identity, strength, quality, and purity statements. Expect clear links between CoA attributes, Process Validation, stability data, and the filed dossier. For APIs, authorities focus heavily on impurities, residual solvents, and stability-driven expiry or retest dates.
Supplements/Nutra. For dietary supplements, 21 CFR Part 111 expects identity testing for each lot of each dietary ingredient and controls for strength, composition, and contaminants. CoAs for both components and finished goods underpin label claims and are central to recall readiness.
Food & beverage. Under 21 CFR Part 117 and GFSI schemes (GFSI, HACCP, BRCGS, SQF), CoAs are often used as evidence that hazards are controlled at the supplier or processing step. Allergen declarations, micro limits, and label-claim checks (net content, nutrition facts) commonly appear alongside shelf-life and FEFO data.
Medical devices. Under 21 CFR 820/QMSR and ISO 13485, CoAs often support purchased-product controls, sterile barrier validation, and functional testing. CoAs must line up with the DMR and DHR, plus UDI data and EU MDR requirements where applicable.
Cosmetics. For MoCRA and ISO 22716, CoAs underpin the Cosmetic Product Safety Report (CPSR) and Product Information File (PIF). Authorities expect clear evidence for impurities, microbiological quality, preservatives, and restricted substances, as well as alignment with claims substantiation.
Chemicals & agrochemicals. CoAs here often reference active content, by-products, stabilisers, and critical physical properties, alongside regulatory identifiers (for example, EPA registration numbers, Restricted Use Pesticide status). Integration with Chemical Management Systems and SDS libraries is common.
6) Supplier CoAs, Verification & Incoming Inspection
Incoming supplier CoAs. For raw materials, excipients, packaging, and intermediates, suppliers frequently provide their own CoAs. These documents feed into Component Release, Incoming Inspection, and Supplier Quality Management (SQM). However, regulators expect more than filing them: organisations must demonstrate a structured Supplier Verification of COAs programme.
Typical patterns include:
- Risk-based supplier classification and Supplier Qualification.
- First-x-lots testing (for example, 3–5 lots) to compare supplier CoA data vs in-house results attribute-by-attribute.
- Defined tolerances and correlation acceptance criteria, documented in Quality Agreements.
- Ongoing re-verification (spot testing, periodic audits, performance scorecards) tied into SCAR where needed.
Reduced or skip-lot testing. Accepting supplier CoAs in place of full in-house testing can be appropriate—but only once the supplier’s process and data have been demonstrated reliable and monitored over time. Inadequate verification, over-reliance on paper, and missing periodic checks are all frequent 483/observation themes.
7) Digital Enforcement, Label Alignment & Machine-Readable CoAs
In a disciplined digital stack, the CoA is compiled by the system of record: LIMS contributes results; MES contributes batch and equipment context; QMS contributes deviation/CAPA outcomes; WMS provides release status and warehouse location; labelling systems pull claims and artwork from approved masters. Attempting to release a lot without a complete CoA—or with a CoA referencing obsolete specs or labels—should be technically blocked via hard-gated electronic pass/fail controls.
Label and CoA reconciliation. For regulated products, the CoA and label must tell the same story: strength, dosage, allergens, storage conditions, and expiry must match. Systems should prevent printing from legacy templates or “manual edits” to labels and instead tie everything back to recipe/label version control. CoA data often feeds into FEFO picking and customer-specific labelling rules.
QR codes, portals & GS1. Many organisations are moving to portal-based, verifiable CoAs. QR or GS1 Digital Link codes on the label resolve to a hosted CoA endpoint that shows the current version, signature status, and history. This approach supports DSCSA, EU FMD, and modern traceability expectations while giving customers immediate confirmation that the CoA is genuine and untampered.
8) Common Failure Modes & How to Avoid Them
- Manual or re-keyed CoAs. Re-keying invites transcription errors and breaks data integrity. Use direct interfaces/APIs from LIMS, MES, and QMS into controlled CoA templates.
- Spec/version drift. Generating CoAs against outdated limits or method versions after changes were approved. Bind CoA generation to live specifications managed under Change Control.
- Label misalignment. CoAs and labels generated from different data sets or local spreadsheets. Enforce a single source of truth for both CoA and labelling.
- Open OOS/OOT investigations. Releasing lots while investigations remain open or before CAPAs are implemented. Block release status in MES/WMS until QA disposition is recorded.
- Over-trusting supplier CoAs. Accepting supplier data without a structured Supplier Verification of COAs programme, correlation studies, and periodic re-verification.
- Editable or locally stored PDFs. CoAs saved to local drives, edited in desktop tools, or lacking audit trails. Use tamper-evident, centrally hosted documents under CSV and Part 11 controls.
- Missing retention & recall linkage. CoAs not easily retrievable for mock recalls, customer complaints, or regulatory inspections. Tie CoAs into record retention/archival and recall readiness frameworks.
9) How Certificates of Analysis Relate to V5
V5 by SG Systems Global generates CoAs directly from source-truth across production, lab, quality, and warehouse operations. Each lot’s history—materials, Batch Weighing tolerances, alarms, in-process controls (IPC), yields, CIP/SIP status—feeds the context section. LIMS results flow via the LIMS interface and EDI/API, preserving method IDs, LOQs, and analyst attribution. QMS contributes deviation/OOS dispositions, CAPA references, and risk assessments. The CoA template is version-controlled, and generation is blocked if the specification, label template, or training/competency status are obsolete.
On the outbound side, Bin / Location Management, Barcode Validation, and ASNs ensure that the CoA attached to a shipment (PDF, QR code, or EDI attachment) matches the actual lots and SSCCs loaded. For APR/PQR and CPV, V5 aggregates CoA attributes (assay trends, micro failure rates, OOTs) into dashboards and SPC control limits so drift is detected long before formal failures.
Incoming materials. For Component Release, supplier CoAs are ingested, parsed, and compared to purchase specifications and Quality Agreements. WMS automatically places discrepant lots in Quarantine/Hold, pushes sampling instructions to LIMS, and prevents use in Batch Tickets until QA releases them. Supplier performance, including CoA accuracy, feeds back into SQM and SCAR processes.
10) Practical CoA Readiness Checklist
Organisations looking to tighten CoA practice can use a simple internal checklist mapped to their QMS and digital systems:
- All specifications and methods are controlled documents under Document Control with clear versioning.
- Each CoA attribute can be traced back to a validated or verified test method with current status.
- Sampling plans are risk-based, documented, and referenced on or from the CoA.
- CoA generation is tightly integrated with MES, LIMS, QMS, and WMS; no offline editing is required to finalise a CoA.
- Label data (Supplement Facts, nutrition facts, strength, allergens) reconciles automatically with CoA data.
- Supplier CoAs are verified through a structured verification programme, not just filed.
- All CoAs are retained, searchable, and immediately available for mock recalls, regulatory inspections, and customer questions.
- Training records show that personnel approving CoAs are qualified, with role-based competence mapped in the Training Matrix.
Related Reading
• Systems & Records: Electronic Batch Record (eBMR) | Batch Manufacturing Record (BMR) | LIMS
• Release & Supplier Control: Batch Release | Component Release | Supplier Verification of COAs
• Quality & Trending: Continued Process Verification (CPV) | Statistical Process Control (SPC) | APR / PQR
• Compliance Foundations: GMP / cGMP | ISO/IEC 17025 | Record Retention & Archival
OUR SOLUTIONS
Three Systems. One Seamless Experience.
Explore how V5 MES, QMS, and WMS work together to digitize production, automate compliance, and track inventory — all without the paperwork.

Manufacturing Execution System (MES)
Control every batch, every step.
Direct every batch, blend, and product with live workflows, spec enforcement, deviation tracking, and batch review—no clipboards needed.
- Faster batch cycles
- Error-proof production
- Full electronic traceability

Quality Management System (QMS)
Enforce quality, not paperwork.
Capture every SOP, check, and audit with real-time compliance, deviation control, CAPA workflows, and digital signatures—no binders needed.
- 100% paperless compliance
- Instant deviation alerts
- Audit-ready, always

Warehouse Management System (WMS)
Inventory you can trust.
Track every bag, batch, and pallet with live inventory, allergen segregation, expiry control, and automated labeling—no spreadsheets.
- Full lot and expiry traceability
- FEFO/FIFO enforced
- Real-time stock accuracy
You're in great company
How can we help you today?
We’re ready when you are.
Choose your path below — whether you're looking for a free trial, a live demo, or a customized setup, our team will guide you through every step.
Let’s get started — fill out the quick form below.































